Cyber-attacks (known as online data breaches) have become more frequent, causing data leaks, network outages, financial losses, and damaging companies’ work, reputation and hinder their ability to recover the stolen data. So far this year, the number of data breaches and cyber-attacks reached more than 878 million records. In December 2020 alone, 148 million data breach records were reported. Generally, data breaches and cyber-attacks can affect different sectors at all levels, and currently, cybersecurity incidents have become a day-to-day struggle for businesses of all sizes.
A recent cybersecurity magazine article pointed out that the global costs of cyber-attack damages might reach billions of dollars yearly. For example, Ransomware damages, malware attacks that expose private information are expected to rise to $20 billion by the end of 2021. The article stated that businesses are expected to fall victim to a ransomware attack every 11 seconds. These attacks might create an extra burden on safety officers’ shoulders to set contingency plans and have practical emergency response plans that encompass Critical Event Management (CEM) solutions to face such threats.

Security Emergency Response Plan
The cybersecurity emergency response plan is a set of actions and instructions designed to help companies prepare, identify, respond, communicate and recover from network security incidents, such as phishing and malware attacks. Every enterprise needs a plan of action to use when emergencies strike. To make this plan successful and bear its fruits, it must highlight different aspects, such as how to respond, what resources to use, and who should be contacted, minimizing damages and responding to incidents as quickly as possible. However, it is still possible that cyber-attacks hit the organization in many ways and levels.
The Power of Critical Event Management Platforms
Critical events such as cyber-attacks can happen at any time and without warning, yet many organizations are not prepared to handle such events. Research studies found that many organizations take a more reactive, ad hoc approach towards applying incident management and response systems beyond IT so that responses during crisis time tend to be slow and disconnected.
Since cybersecurity incidents continue to grow in number and severity, organizations must utilize practices that allow them to identify, respond, and mitigate these types of critical events while becoming more resilient and protecting against future events. Therefore, cybersecurity management needs to employ a combination of automated critical event management systems, data protection tools, and human-driven efforts to manage such events effectively.
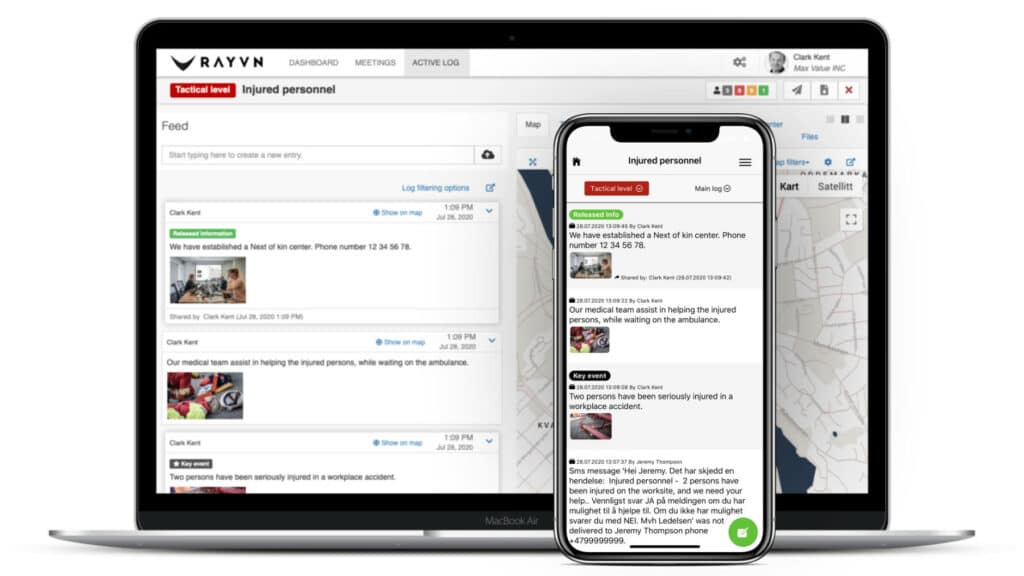
The critical event management process typically starts with an alert when an incident occurs. From there, incident responders investigate and analyze the incident to determine its scope, assess damages, and develop a plan for mitigation and further prevention. In this case, critical event management applications, such as RAYVN, will play a crucial role in maintaining an open and mutual communication line between internal and external stakeholders and lead to a better decision during the cyber-incident time.
Critical Event Management Offerings
Critical event management platforms help organizations to direct communication to stay operationally sound during cyber-attacks. It applies to different aspects as follows:
- Incident management: Critical event management platforms offer dynamic incident response capacity, with a high degree of automation that draws on multiple integrated systems, workflows, documentation, and communications.
- Build alliances: On one hand, critical event management can unify the internal collaborative effort of different functions to provide the expertise; for example, it can help to create a joint response team that engages across the Chief Security Officer, Chief Information Security Officer (CISO), Chief Information Officer, and Human Resources (HR), etc. to discover and handle cyber-attack. On the other hand, this team can collaborate with external stakeholders such as legal, insurance, public relations, regulators, suppliers, partners, and local authorities at the very least to mitigate the impact of cyber-attacks.
- Safety: By combining the ability to set up your Emergency response organization in different locations with a notification system, businesses can alert employees on their devices through multiple platforms to provide them with the needed directions to ensure the assets’ security.
The Human Firewall
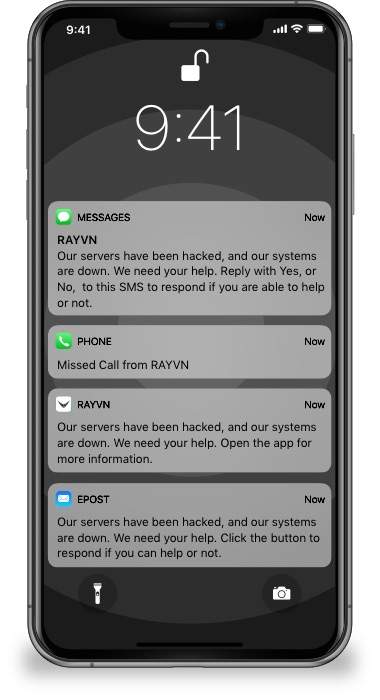 While organizations must invest in protection applications, businesses need to invest in their human-firewalls as part of personnel’s social engineering to protect their networks and valuable data effectively. As the first line of defense, employees must keep a business safe from a malicious source. This plan requires businesses to conduct continuous cybersecurity training to enhance a cybersecurity culture and cybersecurity awareness. Hence, cybersecurity culture plays a crucial role in ensuring that everyone in your organization is aware of potential threats that might hit at any time, understand the urgency of cybersecurity, know their role in maintaining it, and how to respond to such threats. It is, thus, essential to involve all departments, employees, and other key stakeholders in protecting your company's valuable and sensitive data.
While organizations must invest in protection applications, businesses need to invest in their human-firewalls as part of personnel’s social engineering to protect their networks and valuable data effectively. As the first line of defense, employees must keep a business safe from a malicious source. This plan requires businesses to conduct continuous cybersecurity training to enhance a cybersecurity culture and cybersecurity awareness. Hence, cybersecurity culture plays a crucial role in ensuring that everyone in your organization is aware of potential threats that might hit at any time, understand the urgency of cybersecurity, know their role in maintaining it, and how to respond to such threats. It is, thus, essential to involve all departments, employees, and other key stakeholders in protecting your company's valuable and sensitive data.
Regular incident-response exercises and training will be an excellent solution to maintain cyberculture. For example, conducting training that acts as a live cyber-attack scenario will educate personnel on how to respond quickly, reach related stakeholders rapidly, and build trust between stakeholders and your employee, which will be a paramount term for safeguarding your business.
Take your safety to the next level
- Notify and engage external and internal stakeholders in critical event handling
- Real-time communication with key stakeholders
- Manage and assign tasks
- Send valuable information to your entire line of service
- Train and simulate critical event handling
- Automatic documentation and reporting
- Monitor the position of your resources
- Review data and statistics
Your 14-day RAYVN free trial!
Test RAYVN and all its features in your organization
Simple sign-up process. You will not need to enter a credit card to sign-up for the trial.
Our support team is here to help you if you have any questions.