Cyber-attacks number among the frequent, persistent threats facing any organization today. The risks are considerable, including data leaks, the disruption of service, network outages, financial losses and reputational damage.
- Data breach According to IBM, the global average cost of a data breach in 2024 is $4.88 million: a 10% increase over last year and the highest total ever.
- Ransomware The average extortion demand per ransomware attack was over $5.2m (£4.1m) in the first half of 2024, according to Comparitech.
- Cyber crime Cybercrime costs could reach US$10.5 trillion (£8.4 trillion GBP) annually by 2025 according to Cybersecurity Ventures.
While any organization is open to attack, recent data shows that certain sectors represent particularly high-value targets, including healthcare, financial, pharmaceuticals, technology, energy and professional services.
Given these risks and costs, any cyber-security incident presents a challenge for HSEQ managers and IT security as well as the C-Suite, especially the CTO/CISO and CEO. Contingency plans and practical emergency response plans need to address such threats by bringing together the relevant teams to address the technical issues as well as alerts and updates to keep the C-suite management in the loop.
At RAYVN, we suggest any organization might benefit from following our closed loop, continuous model for emergency preparedness and critical event management when it comes to cyber incidents.
PLAN:
Create a Security Emergency Response Plan
Proactive measures are in place to secure the network, IT services and digital operations, but any organization faces cyber-security threats on a daily basis. The cybersecurity emergency response plan is a set of actions and instructions designed to help companies prepare, identify, respond, communicate and recover from network security incidents, such as phishing and malware attacks. Every enterprise needs a plan of action to use when emergencies strike.
To make this plan successful, it must include the action steps, such as how to respond, what resources to use, who should be contacted, how to minimize damage and steps to resolve the incident as quickly as possible–all the while maintaining continuity of services. A secure, real-time critical event management system helps everyone to deliver a coordinate response according to plan. Crucially, a critical event management solution needs to be secure—accessible even when the organization network goes down-–for a truly robust cybersecurity incident strategy and plan.
Prepare:
Run regular training exercises and drills
 Critical events such as cyber-attacks can happen at any time and without warning, yet many organizations are not prepared to handle such events. Some organizations still take a reactive, ad hoc approach to incident management and response. It’s important that IT security plans and preparation are coordinated fully and integrated into overall emergency preparedness and critical event management. A critical event management platform, such as RAYVN, enables organizations to run training drills and exercises so that everyone in the emergency response team can deliver a fully coordinated response when it counts.
Critical events such as cyber-attacks can happen at any time and without warning, yet many organizations are not prepared to handle such events. Some organizations still take a reactive, ad hoc approach to incident management and response. It’s important that IT security plans and preparation are coordinated fully and integrated into overall emergency preparedness and critical event management. A critical event management platform, such as RAYVN, enables organizations to run training drills and exercises so that everyone in the emergency response team can deliver a fully coordinated response when it counts.Respond:
Gain instant situational awareness & collaborate securely
The critical event management process typically starts with an alert when an incident occurs. From there, incident responders investigate and analyze the incident to determine its scope, assess damages, and agree on a plan to resolve the incident. A critical event management solution such as RAYVN plays a crucial role in maintaining an open communication line between internal and external stakeholders. In turn, this leads to a better decision during the cyber-incident time. RAYVN’s collaboration feature provides secure, real-time access to the solution for everyone so that any member of the team can help to resolve the incident. To support cyber-security, RAYVN enables any organization to invite an external stakeholder or partner to join the emergency response network free-of-charge.
RECOVER:
Defend against disruption when it counts
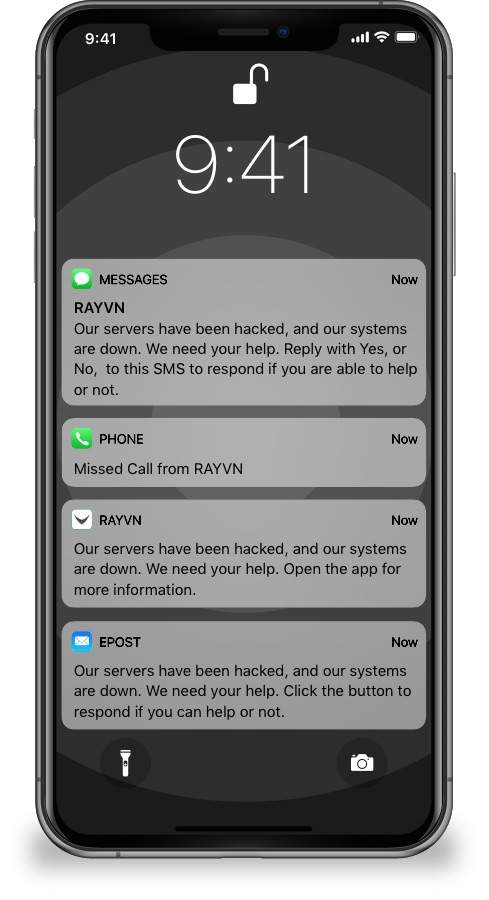 A secure critical event management solution enables the organization to resolve cyber-attacks and recover, whether that’s by recovering backup systems and data, restoring power or other measures, even when the organization’s network goes down. Meanwhile, the emergency notification system can be used to keep employees aware of the status. RAYVN also makes sure that internal and external stakeholders can be given relevant updates in real-time.
A secure critical event management solution enables the organization to resolve cyber-attacks and recover, whether that’s by recovering backup systems and data, restoring power or other measures, even when the organization’s network goes down. Meanwhile, the emergency notification system can be used to keep employees aware of the status. RAYVN also makes sure that internal and external stakeholders can be given relevant updates in real-time.
Overall, such a critical event management solution means that everyone in the organization, as well as customers and/or citizens, can be confident that any IT disruption is being handled effectively. Protecting the reputation of the organization is a key aspect of the ability to deal with disruption, maintain continuity of service and recover swiftly from any threat.
ASSESS & ADAPT:
Reporting Enables Organizations to Improve Security
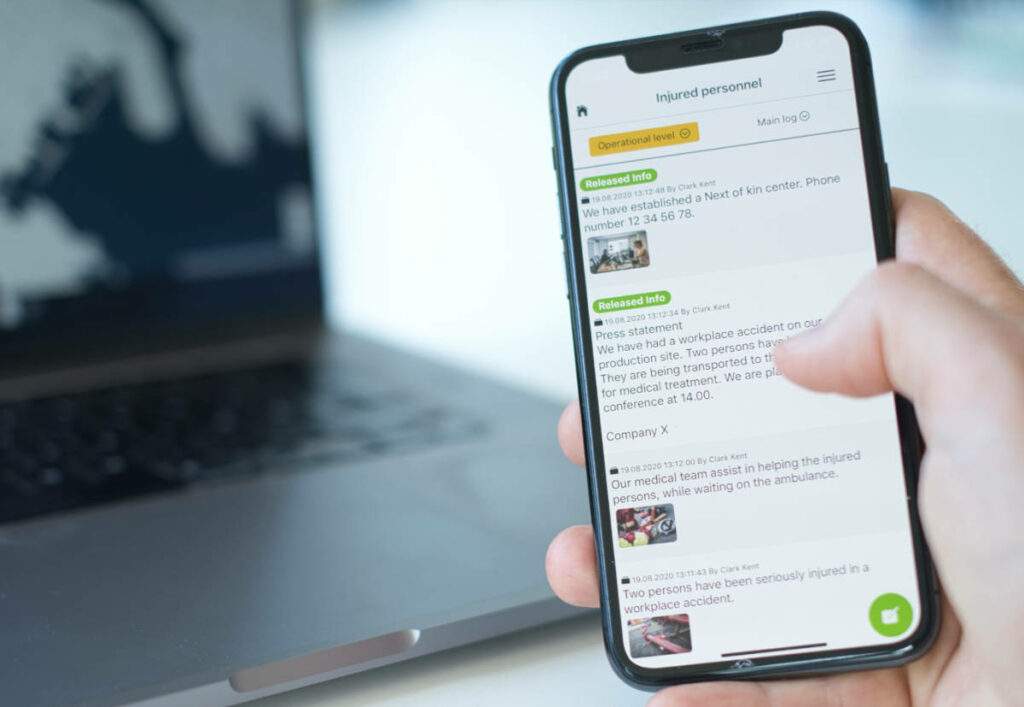
For compliance, insurance, shareholder management and security purposes, reporting plays a critical role in post-incident review. A critical event management system that provides analytics as well as captures time-stamped logs of decisions, actions and communications taken is absolutely essential for the purposes of accountability, review and improvements for the future. Any learnings can be folded back into the IT security and incident management plans and inform strategies for preparedness and training for the future.
Cultivate Cyber-Resilience: The Human Firewall
 While organizations must invest in security applications, businesses need to invest in their human-firewalls as part of personnel’s social engineering to protect their networks and valuable data effectively. As the first line of defense, employees must keep a business safe from a malicious source. This plan requires businesses to conduct continuous cybersecurity training to enhance a cybersecurity culture and cybersecurity awareness.
While organizations must invest in security applications, businesses need to invest in their human-firewalls as part of personnel’s social engineering to protect their networks and valuable data effectively. As the first line of defense, employees must keep a business safe from a malicious source. This plan requires businesses to conduct continuous cybersecurity training to enhance a cybersecurity culture and cybersecurity awareness.
A robust cybersecurity culture plays a crucial role in ensuring that everyone in your organization is aware of potential threats that might strike at any time, understand the urgency of cybersecurity, know their role in maintaining it, and understand how to respond to threats. All departments, employees and key stakeholders need to invest time and energy into protecting the organization's valuable and sensitive data.
Regular incident-response exercises and training is an excellent solution to maintain a proactive, risk-ready cyberculture. For example, conducting training that acts as a live cyber-attack scenario will educate personnel on how to respond quickly, reach related stakeholders rapidly and coordinate seamlessly to protect security and defend against disruption.
Take cyber-security to the next level
- Build out the emergency response network in advance
- Engage in real-time communication with key stakeholders during any incident
- Manage and assign tasks securely
- Send instant notifications across the organization
- Run regular IT security drills and exercises to be improve preparedness
- Rely on automated documentation and time-stamped logs to quickly and efficiently generate status updates and
- post-incident reporting
- Review data and statistics easily with a secure digital critical event management solution
Try RAYVN for free
Wondering if RAYVN is the right solution?
Get a fully functional RAYVN account to test drive its key features, verify it meets your needs, and see how easy it is to digitalize your emergency response plan.